5 strong arguments for our software
Outerscore is the perfect solution for companies that want….
Autopilot compliance, cost and quality monitoring
Outerscore’s mission is to make it difficult to do the wrong and easier to do the right thing. This specifically relates to workforce compliance. We’ve fused deep legal and sourcing expertise with latest technology
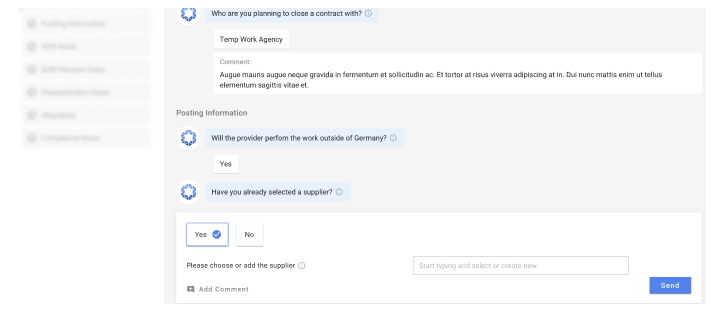
Outerscore Gateway:
The single entry point for any external service or worker requisition across the company. No further decision wizard, but score-based contractual recommendations, process governance and supplier matching
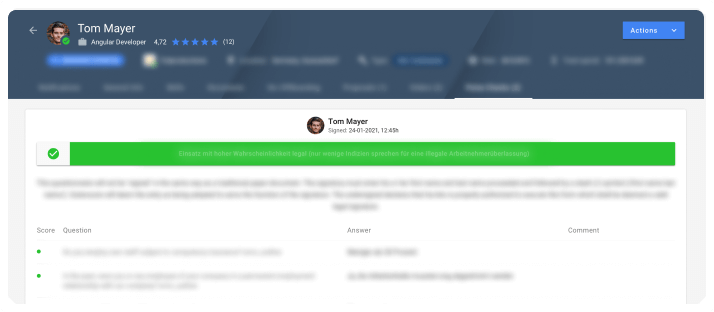
Pulse Checks:
Scheduled, automated pulse checks for suppliers, workers and hiring managers to assure compliance, task assignment & completion and regular feedback during ongoing engagements

Anomaly Engine:
Configure real-time monitoring of risks, costs and quality. Track assignments, workers and suppliers gainst predefined criteria. Automatically spot issues with classifications, pay rates, budgets, max. tenure, certifications, trainings, performance and many more.
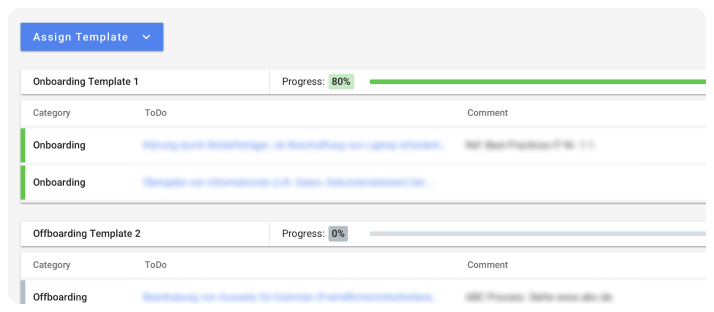
Guided On-/Offboardings:
Digitized on-/offboarding workflows including self-disclosures, document up- or downloads. Automated validity checks, electronic signatures and many more. Fully configurable fields, workflows and event triggering
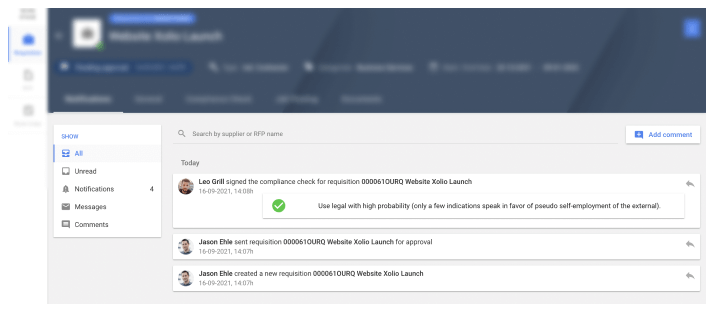
Audit Trail:
Convenient recording of all inputs, modifications and decisions. Proof of proper process implementation. Easy access to greater detail and on-demand availability of all documents, approvals, signatures and more
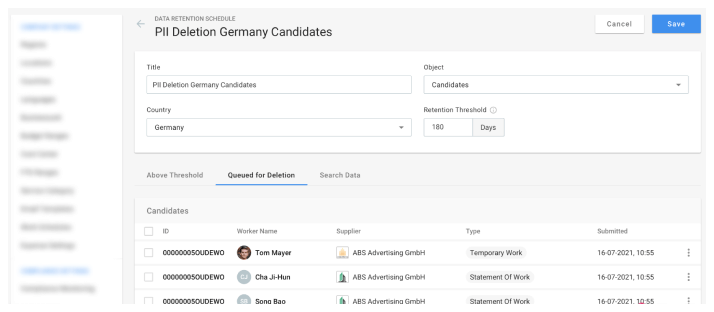
PII & Data Retention:
Full data ownership for suppliers and workers to maintain compliance with GDPR. Configurable data retention periods to pyseudonymize and anonymize personal identifiable information (PII) automatically
Supercharged SOW Management
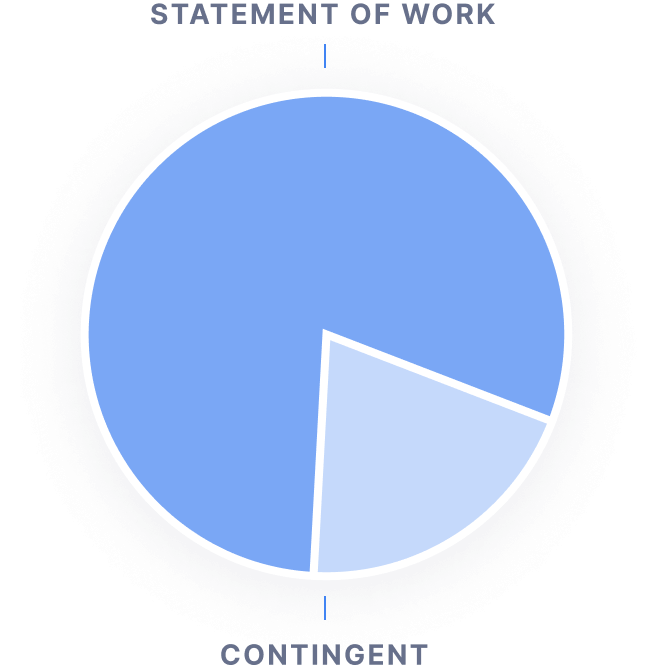
Traditional vendor management systems mainly focus on common forms of contingent labor like temp workers managed by staffing suppliers or agencies. However 60-70% of the service spend (in value) in enterprises are typically SOW-based services and projects.
Incumbent technology hasn’t kept up with the need for a user-friendly way to manage deliverable-, milestone- or unit-based service delivery. Whether you are aiming to manage consultants, a large IT project, marketing agencies or a recurring outsourcing service fee:
Outerscore transforms SOW management with smart bid templates that make even complex service bundles shoppable. Our solution differentiates significantly from competitors and can be considered as best-in-class.
Project-specific dashboards provide real-time data on project progress, budgets and approved order modifications.
Elegant, Modular All-In-One System
Having multiple systems for requesting contractors, full-time workers, and project-based workers is cumbersome and opens you up to risk, not to mention frustration from managers and talent. We provide a central platform oriented around work to be done, not engagement types. Algorithms and a guided buying process translate hiring managers’ needs into the right setup with the right supplier or talent at the right price and right quality.
A modular, flexible system with self-service configurability enables admin users to build their very own, individual system and shorten deployment time. Packaged components (Temp, IC, SOW) can be individually used or connected, as needed. Fully integrated workflows for different engagement types assure a complete picture on all external worker, supplier and engagement data – across all types of contracts.

APIs as First-Class Citizens
Outerscore can be used stand-alone or integrated into your existing tech ecosystem: Connect with your favorite procurement, HR, accounting or reporting platforms to reduce manual tasks, streamline workflows, and make life a lot easier with just a few clicks.
We have engineered pre-build connectors and endpoints to ensure seamless integration with third party software. While building the platform we took an API-first approach. All data can be imported or exported via CSV or REST interface. We integrate with your existing solutions much faster than you might expect.

ISMS – No Security Concerns
We build, manage and maintain our application based on an information security management system (ISMS) that has been independently audited and certified according to ISO27001.
The ISMS assures a set of security controls that protect the confidentiality, availability, and integrity of confidential, personal, and sensitive data from being leaked, damaged, destroyed, or exposed to harmful elements.

Secure Architecture: Our tiered architecture provides multiple layers of protection. Each application operates in its own silo, heavily protected from the internet by our front-end load balancers, layer-3 and web application firewalls and intrusion detection systems
Encrytion in Transit and at Rest: Any data that is transferred over the internet uses industry-standard encryption: All traffic in transit uses the latest secure cipher algorithms (TLS 1.2) and we use per customer (AES-256) keys to encryt data on disk
Audit Logging: Every change in the system and all data transfers via API to other systems are logged using latest Amazon Web Services technology like AWS CloudWatch and AWS CloudTrail. All log data is stored for at least 14 days
Attribute-based Access Control: Outerscore maintains a fine grained access control using a combination of authentication, authorization, and entitlement mechanisms. We support several authentication options such as Okta, OneLogin, or SecureAuth to provide seamless SSO
Performance and Availability: Our infrastructure-as-code (IaC) approach allows us to restore or launch our entire infrastructure in less than 30 min. Utilizing the leading enterprise business cloud – AWS – allows us to make use of best-in-class cloud hosting security standards
Security Assessments and Tests: We continuous test our application for security flaws and potential vulnerabilities. Every line of code must pass rigorous testing in three different environments before it is deployed to our customers

